Understanding KeepKey’s PIN Security System
Technical Overview
The KeepKey implements a sophisticated PIN entry system that protects against various attack vectors:
- Physical observation (shoulder surfing)
- USB-based keyloggers
- Screen content analysis
- Malware and spyware
- Brute force attempts
PIN Architecture
Your PIN can be 1-9 digits long, with each digit ranging from 0-9. This provides:
- Maximum combinations: 10^9 (1 billion) for 9-digit PINs
- Minimum recommended: 10^4 (10,000) for 4-digit PINs
- Three-attempt limit before device reset
The Cipher System
How It Works
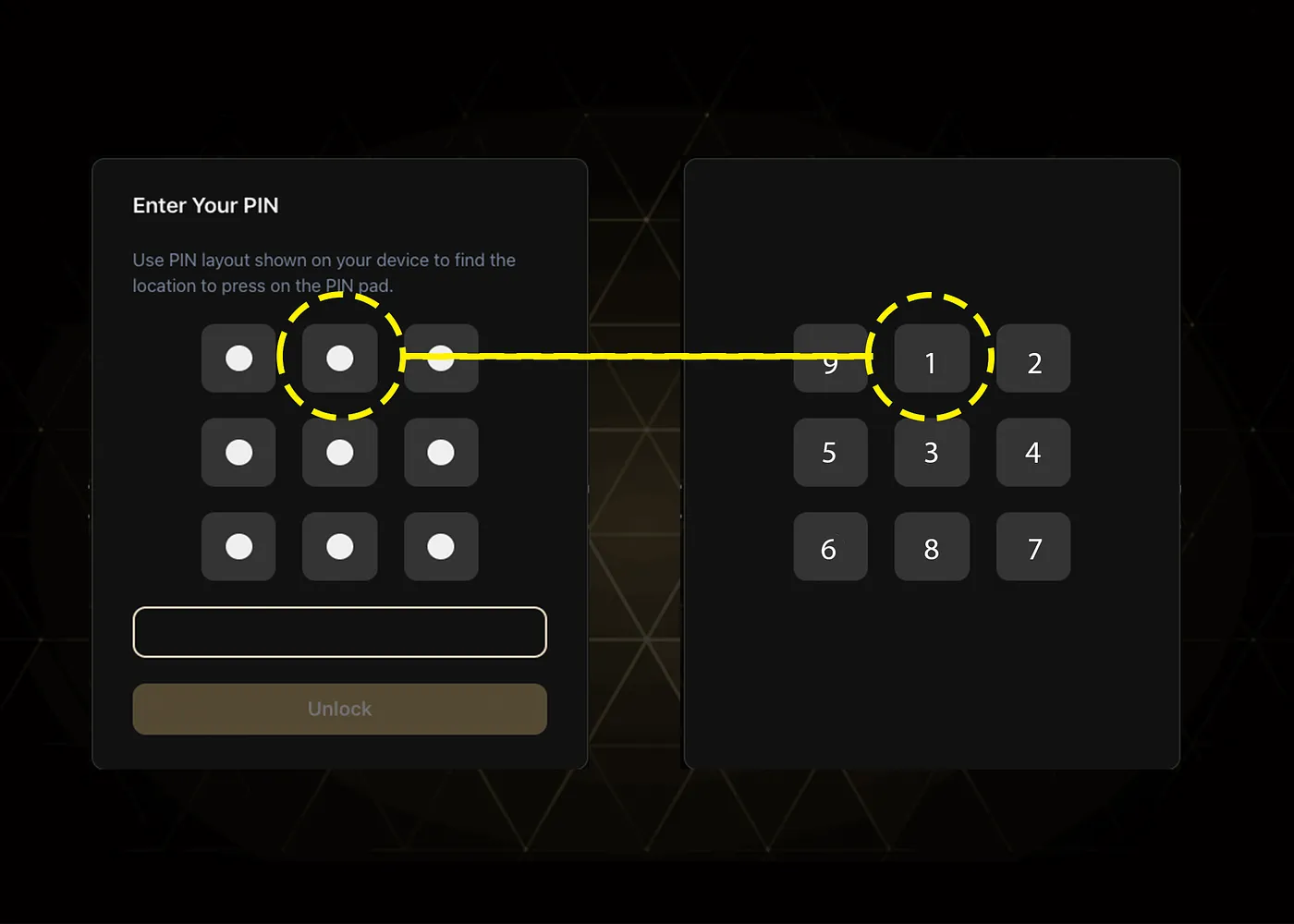
The KeepKey employs a dynamic cipher system for PIN entry:
-
Randomized Matrix
- 3x3 grid of numbers (0-9)
- Positions scrambled on every connection
- Numbers only visible on device screen
-
Dual Display Protection

Anti-Analysis Protection
The PIN display implements several security measures:
-
Pixel Balance Technology
- Equal number of lit/unlit pixels per row
- Prevents power analysis attacks
- Defeats USB resistance monitoring
-
Visual Inversion
- Numbers displayed twice with inversion
- Maintains constant power consumption
- Thwarts side-channel attacks
Security Implementation
Zero-Trust Model
The KeepKey operates under a zero-trust security model:
- Assumes host computer is compromised
- Requires on-screen verification for all actions
- Never exposes sensitive data to host
Critical Security Note: A hardware wallet without a screen cannot provide adequate security. The screen-to-processor connection is fundamental to the security model.
PIN Entry Process
-
Connection Phase
- Device generates random cipher
- Displays scrambled keypad
- Awaits user input
-
Input Validation
- Each digit processed independently
- Position mapped through cipher
- No direct number transmission
-
Confirmation Process
- New cipher generated for confirmation
- Prevents pattern analysis
- Requires second entry match

Best Practices
PIN Selection
-
Length Considerations
- Minimum: 4 digits
- Recommended: 8 digits
- Maximum: 9 digits
-
Avoid Common Patterns
- Sequential numbers
- Repeated digits
- Birth dates
- Phone numbers
Usage Guidelines
-
Physical Security
- Shield screen during entry
- Verify surroundings
- Use in private when possible
-
Device Protection
- Verify screen content matches expectations
- Never enter PIN on unofficial interfaces
- Keep track of attempt count
Recovery Preparation
-
Device Reset Protocol
- Three wrong attempts trigger reset
- All data wiped from device
- Recovery phrase required for restoration
-
Backup Requirements
- Keep recovery phrase secure
- Document PIN securely
- Plan for device loss/reset
Security Warning: Never share your PIN or recovery phrase with anyone, including KeepKey support staff. The cipher system ensures secure entry even on compromised computers, but only if you maintain PIN confidentiality.